In April, I stumbled over a Cross-Site Scripting vulnerability on the Mozilla Developer Network!
Due to improper input validation mechanisms an attacker could temporarily inject own code into user browser sessions with required user interaction using manipulated URLs:

which could then be used e.g. for phishing purposes using a temporary defacement:
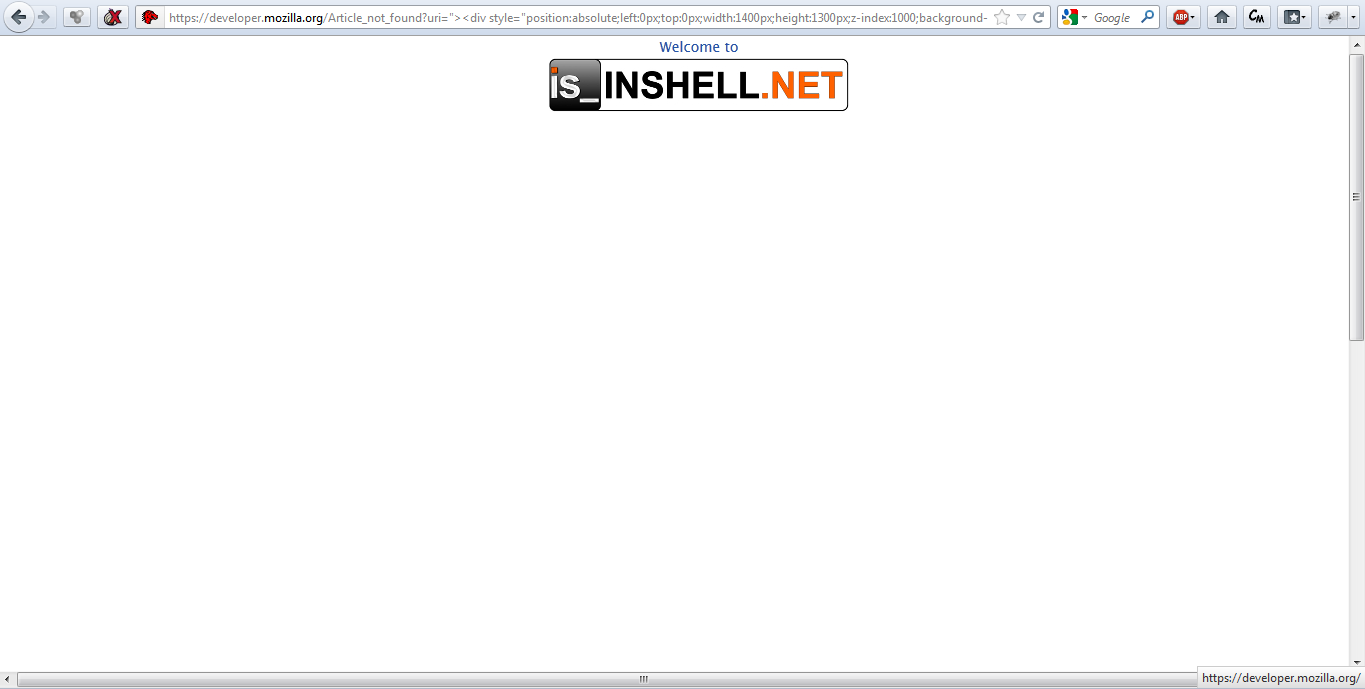
But the injection itself was very limited here, because the web-engine of the Developer Network successfully removes JavaScript code from the input, so there has never been a direct security problem for the accounts of the Developer Network! But anyways even the possibility of manipulating the visible content and referencing for example other malicious webpages or something like this could harm unexperienced users who visit the Developer Network.
Immediately after the finding, I noticed the Mozilla developers through their bugzilla system and received an answer – well, not as fast as Sophos did, but the the timeframe was short enough to say that they care about even smaller bugs.
Now Mozilla has completely changed the Developer Network infrastructure (did you notice the downtime on 8 May 😉 ? ), and fixed the issue as a part of this change.
I would like to thank Reed Loden and Luke Crouch of the Mozilla Team for the very friendly and professional way of dealing with my report. Too bad this bug was not eligible for your bug-bounty program 🙁
