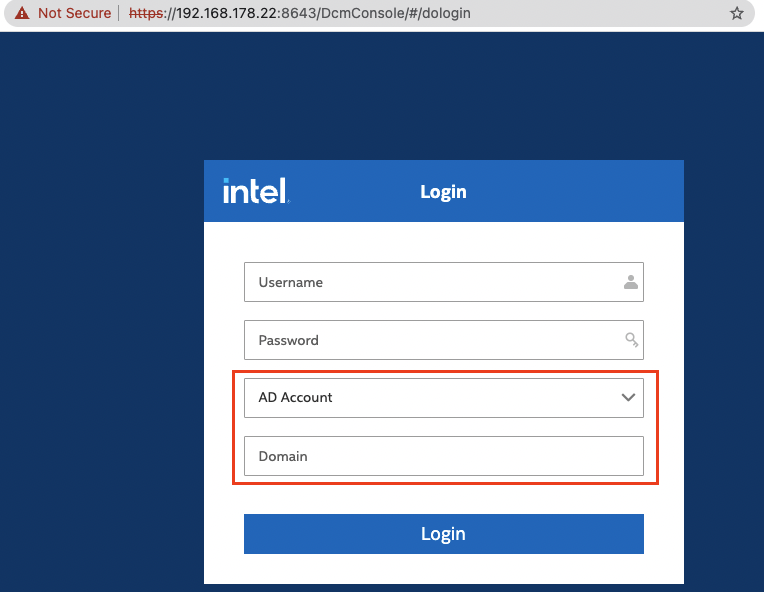
by Julien Ahrens | Wednesday, November 23, 2022 | Bug Bounty, CVE
This small series of two blog posts covers an entire vulnerability chain to go from unauthenticated user to full remote code execution against Intel’s Data Center Manager (up to version 4.1.1.45749).The chain’s first vulnerability bypasses DCM’s entire authentication process.
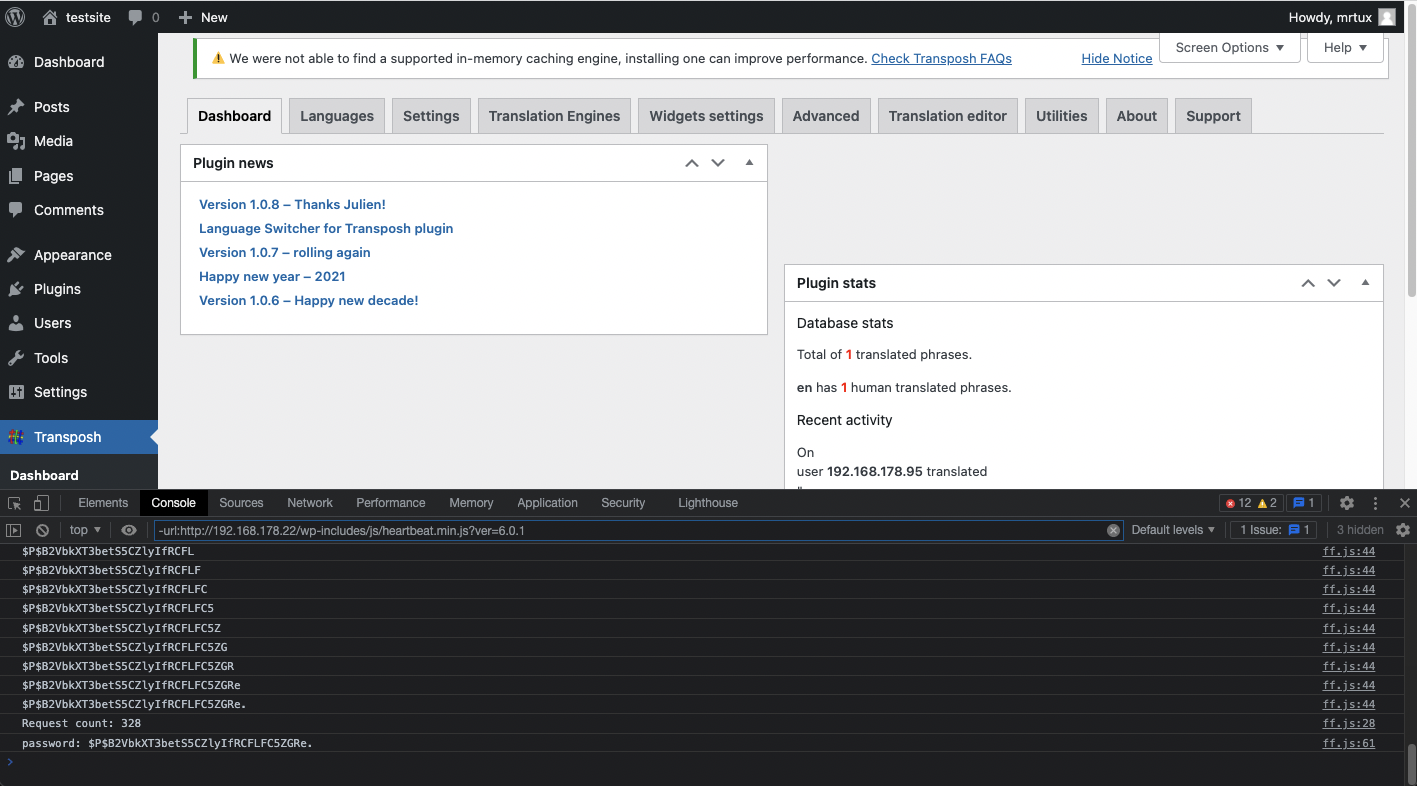
by Julien Ahrens | Friday, July 22, 2022 | Bug Bounty
Introduction You probably have read about my recent swamp of CVEs affecting a WordPress plugin called Transposh Translation Filter, which resulted in more than $30,000 in bounties: [CVE-2021-24910] Transposh <= 1.0.7 “tp_tp” Unauthenticated Reflected Cross-Site...

by Julien Ahrens | Friday, April 22, 2022 | Certifications
Introduction This is a review of the Advanced Web Attacks and Exploitation (WEB-300) course and its OSWE exam by Offensive-Security. I’ve taken this course because I was curious about what secret tricks this course will offer for its money, especially...
by Julien Ahrens | Friday, November 13, 2020 | Bug Bounty
This is the story about how I’ve chained a seemingly uninteresting request smuggling vulnerability with an even more uninteresting header-based XSS to redirect network-internal web site users without any user interaction to arbitrary pages. This post also...
by Julien Ahrens | Monday, September 14, 2020 | Advisory, CVE
You have probably read one or more blog posts about SSRFs, many being escalated to RCE. While this might be the ultimate goal, this post is about an often overlooked impact of SSRFs: application logic impact. This post will tell you the story about an unauthenticated...





