by Julien Ahrens | Monday, August 26, 2024 | Bug Bounty, CVE, Exploit
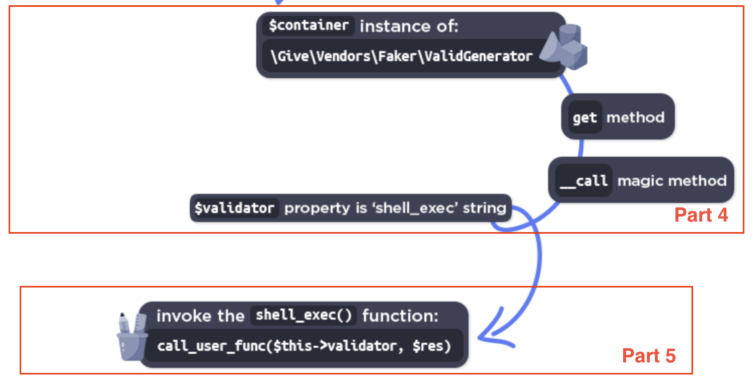
A few days ago, Wordfence published a blog post about a PHP Object Injection vulnerability affecting the popular WordPress Plugin GiveWP in all versions <= 3.14.1. Since the blog post contains only information about (a part) of the POP chain used, I decided to take a look and build a fully functional Remote Code Execution exploit. This post describes how I approached the process, identifying the missing parts and building the entire POP chain.
by Julien Ahrens | Monday, July 3, 2023 | Exploit, Patch Diffing
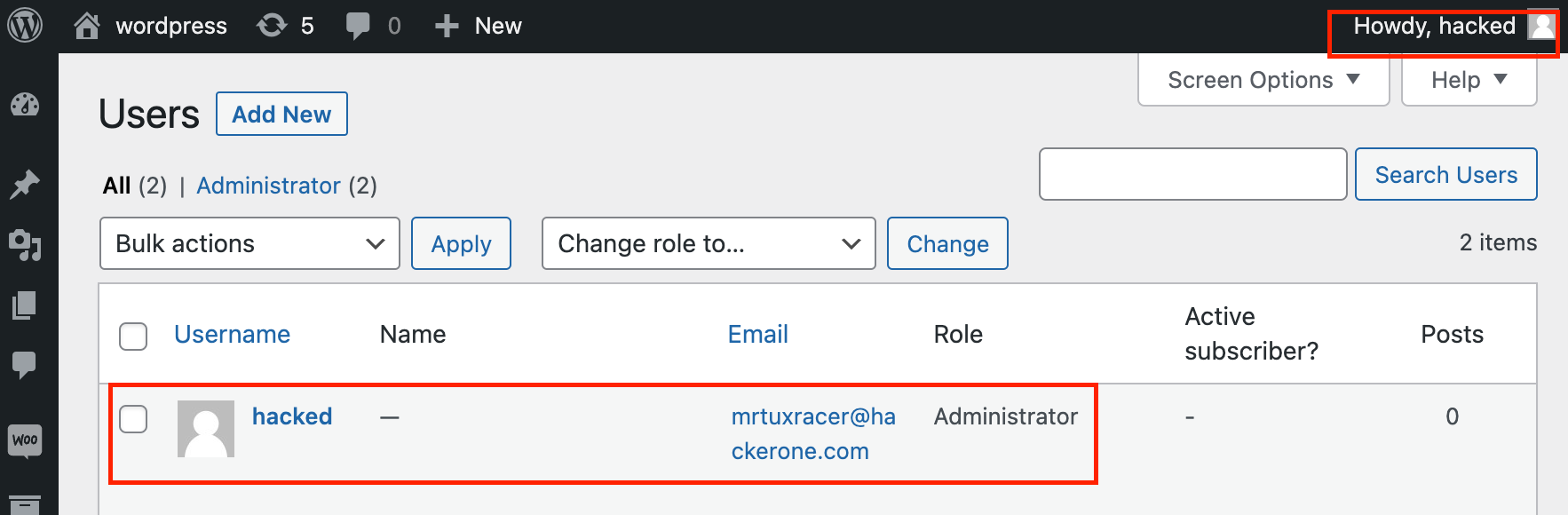
Back in March 2023, I noticed an interesting security advisory that was published by Wordfence about a critical “Authentication Bypass and Privilege Escalation” (aka CVE-2023-28121) affecting the “WooCommerce Payments” plugin which has more...
by Julien Ahrens | Wednesday, April 12, 2023 | Advisory, CVE, Exploit
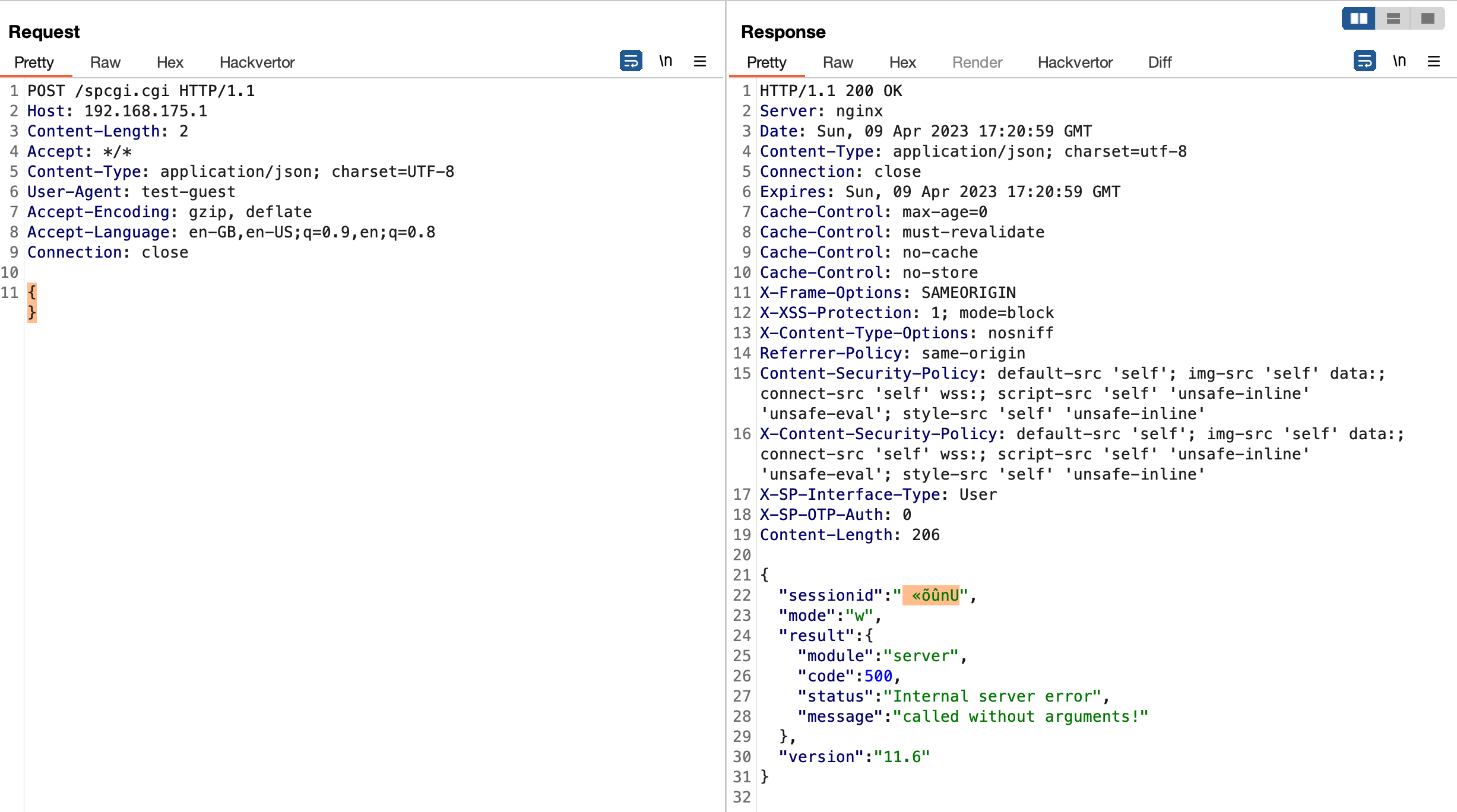
While my last finding affecting SecurePoint’s UTM was quite interesting already, I was hit by a really hard OpenSSL Heartbleed flashback with this one. The following exploit works against both the admin portal on port 11115 as well as the user portal on port...
by Julien Ahrens | Tuesday, April 11, 2023 | Advisory, CVE, Exploit
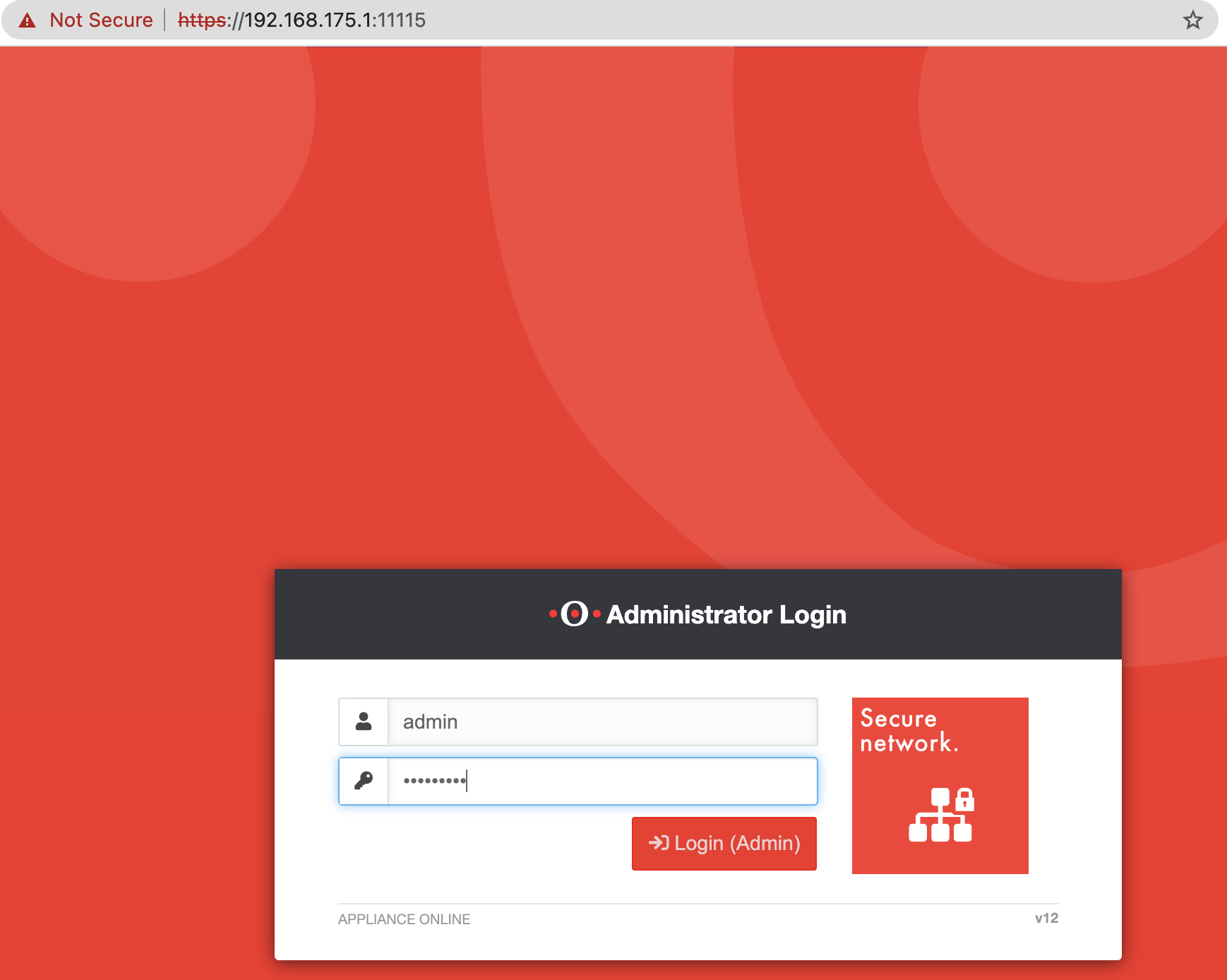
While working on a recent customer engagement, I discovered two fascinating and somewhat weird bugs in SecurePoint’s UTM firewall solution. The first one, aka CVE-2023-22620, is rated critical for an attacker to bypass the entire authentication and gain access...
by Julien Ahrens | Monday, May 13, 2019 | CVE, Exploit
I came across an unauthenticated Remote Code Execution vulnerability (called CVE-2018-7841) on an IoT device which was apparently using a component provided by Schneider Electric called U.Motion Builder. While I’ve found it using my usual BurpSuite foo, I later...
by Julien Ahrens | Saturday, May 31, 2014 | Exploit
During the last few days a lot of nice Remote Exploits have been released over at Exploit-DB by one of my followers Harold aka superkojiman targeting applications by EFS Software Inc. First of all: Kudos to Harold, you did a really nice job :-)! As I...




